이전글: Minikube 클러스터와 도구준비 - https://hibuz.com/minikube-install/
Istio 다운로드
- 최신 릴리즈 다운로드
$ curl -L <https://istio.io/downloadIstio> | sh -
# 특정버전 또는 프로세서 아키텍처 선택 다운로드
# curl -L <https://istio.io/downloadIstio> | ISTIO_VERSION=1.6.8 TARGET_ARCH=x86_64 sh -2. istioctl 클라이언트 PATH 에 추가
cd istio-1.10.0
# 매번 PATH를 설정하지 않고 쉘이 시작될 때마다 실행되는 ~/.zshrc 또는 ~/.bashrc 에 추가하면 편함
$ export PATH=$PWD/bin:$PATH
# Istio 버전 확인
$ istioctl version
no running Istio pods in "istio-system"
1.9.5
참고: 버전 조회시 unable to retrieve Pods 가 발생하면 minikube start로 k8s 클러스터 실행
Istio Operator로 설치
공식문서와 다르게 새로운 버전의 설치 업그레이드 및 제거를 위해 Operator CR만 간단히 업데이트하는 방식으로 Operator 가 설치를 관리할 수 있는 방식을 사용합니다.
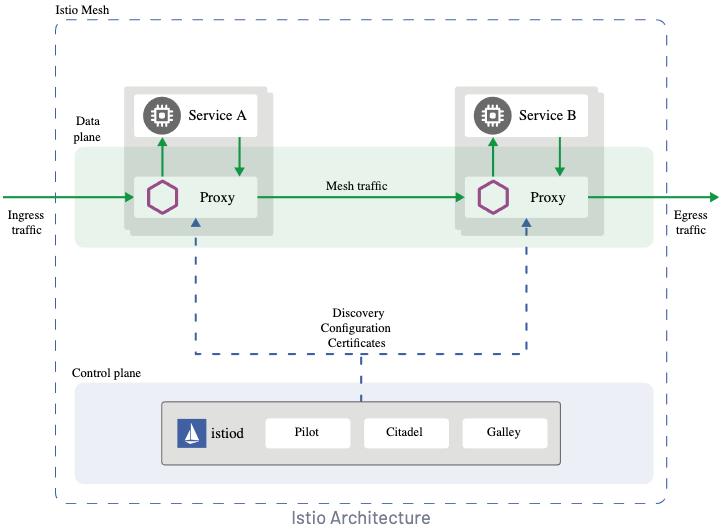
- Operator 초기화
# 삭제시 revision으로 삭제 가능하도록 꼭 기입
$ istioctl operator init --revision 1-10-0
Installing operator controller in namespace: istio-operator using image: docker.io/istio/operator:1.10.0
Operator controller will watch namespaces: istio-system
2021-05-27T21:39:09.061803Z info proto: tag has too few fields: "-"
✔ Istio operator installed
✔ Installation complete
# operator controller pod 조회
$ kubectl get pods --namespace istio-operator \\
-o=jsonpath='{range .items[*]}{.metadata.name}{":\\t"}{range .spec.containers[*]}{.image}{", "}{end}{"\\n"}{end}'
istio-operator-1-10-0-74994f6764-m9jwk: docker.io/istio/operator:1.10.0,
2. IstioOperator 설치
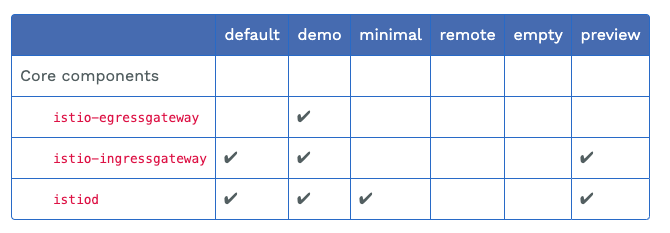
# demo profile로 설치하거나 default profile에 egressgateway 활성화 해서 커스텀도 가능
$ kubectl apply -f - <<EOF
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
namespace: istio-system
name: istio-controlplane-1-10-0
spec:
revision: 1-10-0 # 새버전 업그레이드를 위한 명시적 revision 설정
profile: default
components:
pilot:
k8s:
resources:
requests:
memory: 3072Mi # 메모리 충분히
egressGateways:
- name: istio-egressgateway # default profile에 빠져있는 egress 도 추가
enabled: true
EOF
istiooperator.install.istio.io/istio-controlplane-1-10-0 created
3. 설치 상태 조회
# 설치 조회 HEALTHY 가 될 때까지 기다리기 (종료: Ctrl + C)
$ kubectl get iop -A -w
NAMESPACE NAME REVISION STATUS AGE
istio-system istio-controlplane-1-10-0 1-10-0 HEALTHY 75s
$ kubectl get po -A | grep istio
NAMESPACE NAME READY STATUS RESTARTS AGE
istio-operator istio-operator-1-10-0-74994f6764-m9jwk 1/1 Running 0 16m
istio-system istio-egressgateway-584b9dcbcb-rszp9 1/1 Running 0 6m19s
istio-system istio-ingressgateway-d87f8fd97-njbjl 1/1 Running 0 6m19s
istio-system istiod-1-10-0-799d598ffb-p7gm8 1/1 Running 0 6m29s
$ kubectl get svc -A | grep istio
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-operator istio-operator-1-10-0 ClusterIP 10.103.174.0 <none> 8383/TCP 15m
istio-system istio-egressgateway ClusterIP 10.97.0.9 <none> 80/TCP,443/TCP 5m37s
istio-system istio-ingressgateway LoadBalancer 10.98.70.51 <pending> 15021:32358/TCP,80:31663/TCP,443:30257/TCP 5m37s
istio-system istiod-1-10-0 ClusterIP 10.98.75.23 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 5m47s
4. Envoy 사이드카 프록시 자동 주입 설정
# rev 미 사용시: kubectl label ns default istio-injection=enabled
$ kubectl label ns default istio.io/rev=1-10-0
namespace/default labeled
# 적용 확인
# rev 미 사용시: kubectl get ns -L istio-injection)
$ kubectl get ns default --show-labels
NAME STATUS AGE LABELS
default Active 11d istio.io/rev=1-10-0,kubernetes.io/metadata.name=default
샘플 애플리케이션 배포
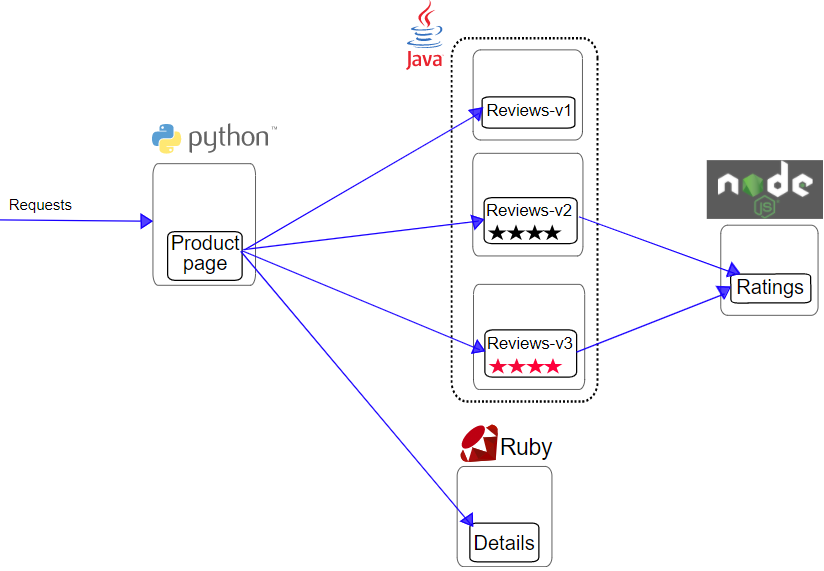
- Bookinfo 배포
$ kubectl apply -f samples/bookinfo/platform/kube/bookinfo.yaml
service/details created
serviceaccount/bookinfo-details created
deployment.apps/details-v1 created
service/ratings created
serviceaccount/bookinfo-ratings created
deployment.apps/ratings-v1 created
service/reviews created
serviceaccount/bookinfo-reviews created
deployment.apps/reviews-v1 created
deployment.apps/reviews-v2 created
deployment.apps/reviews-v3 created
service/productpage created
serviceaccount/bookinfo-productpage created
deployment.apps/productpage-v1 created
2. Pod 이 준비되면 Istio 사이드카와 함께 배포 됨
$ kubectl get services
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
details ClusterIP 10.107.138.111 <none> 9080/TCP 4m36s
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 11d
productpage ClusterIP 10.97.40.144 <none> 9080/TCP 4m36s
ratings ClusterIP 10.101.43.221 <none> 9080/TCP 4m36s
reviews ClusterIP 10.109.78.110 <none> 9080/TCP 4m36s
and
$ kubectl get pods
NAME READY STATUS RESTARTS AGE
details-v1-79f774bdb9-97jws 2/2 Running 0 5m24s
productpage-v1-6b746f74dc-b9glg 2/2 Running 0 5m23s
ratings-v1-b6994bb9-vgt5n 2/2 Running 0 5m24s
reviews-v1-545db77b95-w5zz9 2/2 Running 0 5m24s
reviews-v2-7bf8c9648f-q9tzc 2/2 Running 0 5m24s
reviews-v3-84779c7bbc-5q6nz 2/2 Running 0 5m23s
and
$ istioctl version
client version: 1.10.0
control plane version: 1.10.0
data plane version: 1.10.0 (8 proxies)
$ istioctl ps
NAME CDS LDS EDS RDS ISTIOD VERSION
details-v1-79f774bdb9-97jws.default SYNCED SYNCED SYNCED SYNCED istiod-1-10-0-799d598ffb-p7gm8 1.10.0
istio-egressgateway-584b9dcbcb-rszp9.istio-system SYNCED SYNCED SYNCED NOT SENT istiod-1-10-0-799d598ffb-p7gm8 1.10.0
istio-ingressgateway-d87f8fd97-njbjl.istio-system SYNCED SYNCED SYNCED NOT SENT istiod-1-10-0-799d598ffb-p7gm8 1.10.0
productpage-v1-6b746f74dc-b9glg.default SYNCED SYNCED SYNCED SYNCED istiod-1-10-0-799d598ffb-p7gm8 1.10.0
ratings-v1-b6994bb9-vgt5n.default SYNCED SYNCED SYNCED SYNCED istiod-1-10-0-799d598ffb-p7gm8 1.10.0
reviews-v1-545db77b95-w5zz9.default SYNCED SYNCED SYNCED SYNCED istiod-1-10-0-799d598ffb-p7gm8 1.10.0
reviews-v2-7bf8c9648f-q9tzc.default SYNCED SYNCED SYNCED SYNCED istiod-1-10-0-799d598ffb-p7gm8 1.10.0
reviews-v3-84779c7bbc-5q6nz.default SYNCED SYNCED SYNCED SYNCED istiod-1-10-0-799d598ffb-p7gm8 1.10.0
3. 여기까지 동작여부 확인: 내부에서 curl 요청 후 응답 HTML 페이지의 <title> 태그로 확인
$ kubectl exec "$(kubectl get pod -l app=ratings -o jsonpath='{.items[0].metadata.name}')" -c ratings -- curl -sS productpage:9080/productpage | grep -o "<title>.*</title>"
<title>Simple Bookstore App</title>
외부에서 애플리케이션 접속
Istio Ingress Gateway를 생성하면 메시 edge의 라우팅 path를 통해 Bookinfo 애플리케이션에 접근 가능
- Istio gateway와 애플리케이션 연결
$ kubectl apply -f samples/bookinfo/networking/bookinfo-gateway.yaml
gateway.networking.istio.io/bookinfo-gateway created
virtualservice.networking.istio.io/bookinfo created
2. Configuration에 문제가 없는지 확인
$ istioctl analyze
✔ No validation issues found when analyzing namespace: default.
3. 새로운 터미널을 열어 로드벨런서 IP 할당을 위한 Minikube 터널링 실행
$ minikube tunnel
Status:
machine: minikube
pid: 29430
route: 10.96.0.0/12 -> 192.168.66.4
minikube: Running
services: [istio-ingressgateway]
4. 로드밸런서 IP 를 확인하고 이를 GATEWAY_IP 환경변수로 설정 및 curl 테스트
$ kubectl get svc istio-ingressgateway -n istio-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-ingressgateway LoadBalancer 10.98.70.51 10.98.70.51 15021:32358/TCP,80:31663/TCP,443:30257/TCP 15h
$ export GATEWAY_IP=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
$ curl -I "http://$GATEWAY_IP/productpage"
HTTP/1.1 200 OK
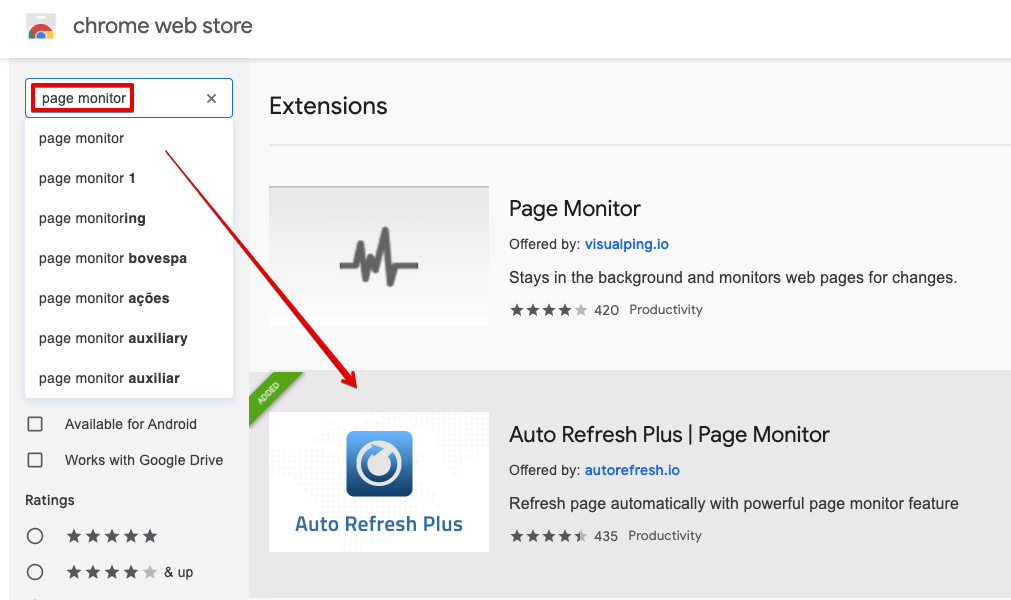
5. 샘플 애플리케이션 테스트용 크롬 확장 설치(Auto Refresh Plus)
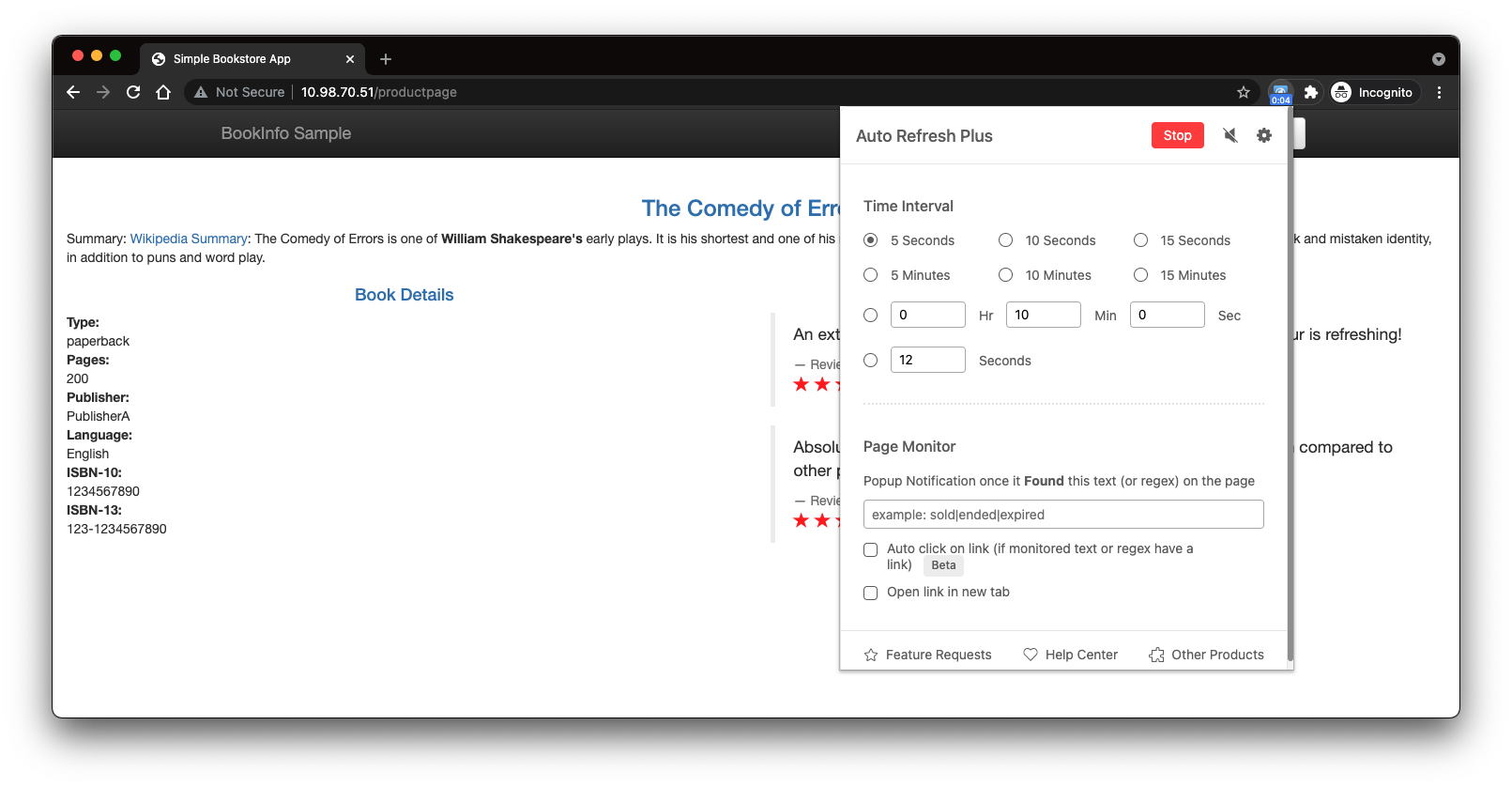
6. Ingress gateway 로드밸런서 IP로 접속 및 일정(5초) 주기로 자동 refresh
대시보드 확인
Istio는 여러 telemetry 애플리케이션과 통합되고 이를 통해 서비스 메시 구조를 이해하고 토폴로지를 표시하여 상태를 분석가능
- Kiali 대시보드와 필요한 Addon 설치
# unable to recognize "samples/addons/kiali.yaml" 발생하고 한번 더 실행
$ kubectl apply -f samples/addons
serviceaccount/grafana created
configmap/grafana created
service/grafana created
deployment.apps/grafana created
configmap/istio-grafana-dashboards created
configmap/istio-services-grafana-dashboards created
deployment.apps/jaeger created
service/tracing created
service/zipkin created
service/jaeger-collector created
customresourcedefinition.apiextensions.k8s.io/monitoringdashboards.monitoring.kiali.io created
serviceaccount/kiali created
configmap/kiali created
clusterrole.rbac.authorization.k8s.io/kiali-viewer created
clusterrole.rbac.authorization.k8s.io/kiali created
clusterrolebinding.rbac.authorization.k8s.io/kiali created
role.rbac.authorization.k8s.io/kiali-controlplane created
rolebinding.rbac.authorization.k8s.io/kiali-controlplane created
service/kiali created
deployment.apps/kiali created
serviceaccount/prometheus created
configmap/prometheus created
clusterrole.rbac.authorization.k8s.io/prometheus created
clusterrolebinding.rbac.authorization.k8s.io/prometheus created
service/prometheus created
deployment.apps/prometheus created
monitoringdashboard.monitoring.kiali.io/envoy created
monitoringdashboard.monitoring.kiali.io/go created
monitoringdashboard.monitoring.kiali.io/kiali created
monitoringdashboard.monitoring.kiali.io/micrometer-1.0.6-jvm-pool created
monitoringdashboard.monitoring.kiali.io/micrometer-1.0.6-jvm created
monitoringdashboard.monitoring.kiali.io/micrometer-1.1-jvm created
monitoringdashboard.monitoring.kiali.io/microprofile-1.1 created
monitoringdashboard.monitoring.kiali.io/microprofile-x.y created
monitoringdashboard.monitoring.kiali.io/nodejs created
monitoringdashboard.monitoring.kiali.io/quarkus created
monitoringdashboard.monitoring.kiali.io/springboot-jvm-pool created
monitoringdashboard.monitoring.kiali.io/springboot-jvm created
monitoringdashboard.monitoring.kiali.io/springboot-tomcat created
monitoringdashboard.monitoring.kiali.io/thorntail created
monitoringdashboard.monitoring.kiali.io/tomcat created
monitoringdashboard.monitoring.kiali.io/vertx-client created
monitoringdashboard.monitoring.kiali.io/vertx-eventbus created
monitoringdashboard.monitoring.kiali.io/vertx-jvm created
monitoringdashboard.monitoring.kiali.io/vertx-pool created
monitoringdashboard.monitoring.kiali.io/vertx-server created
2. 새로운 터미널 창을 열어 Kiali 대시보드 열기
$ istioctl dashboard kiali
<http://localhost:20001/kiali>
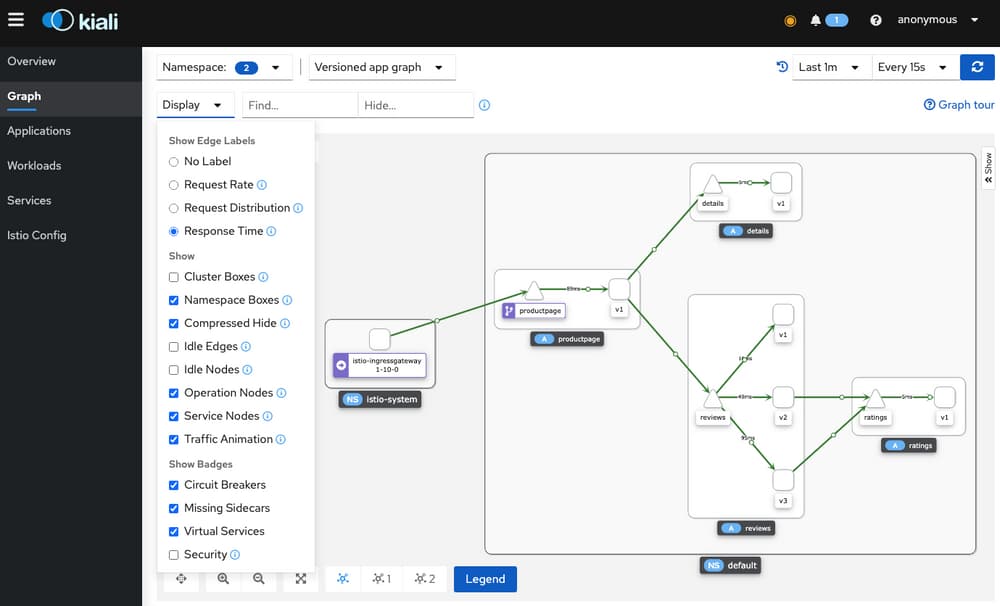
3. Graph 메뉴에서 확인
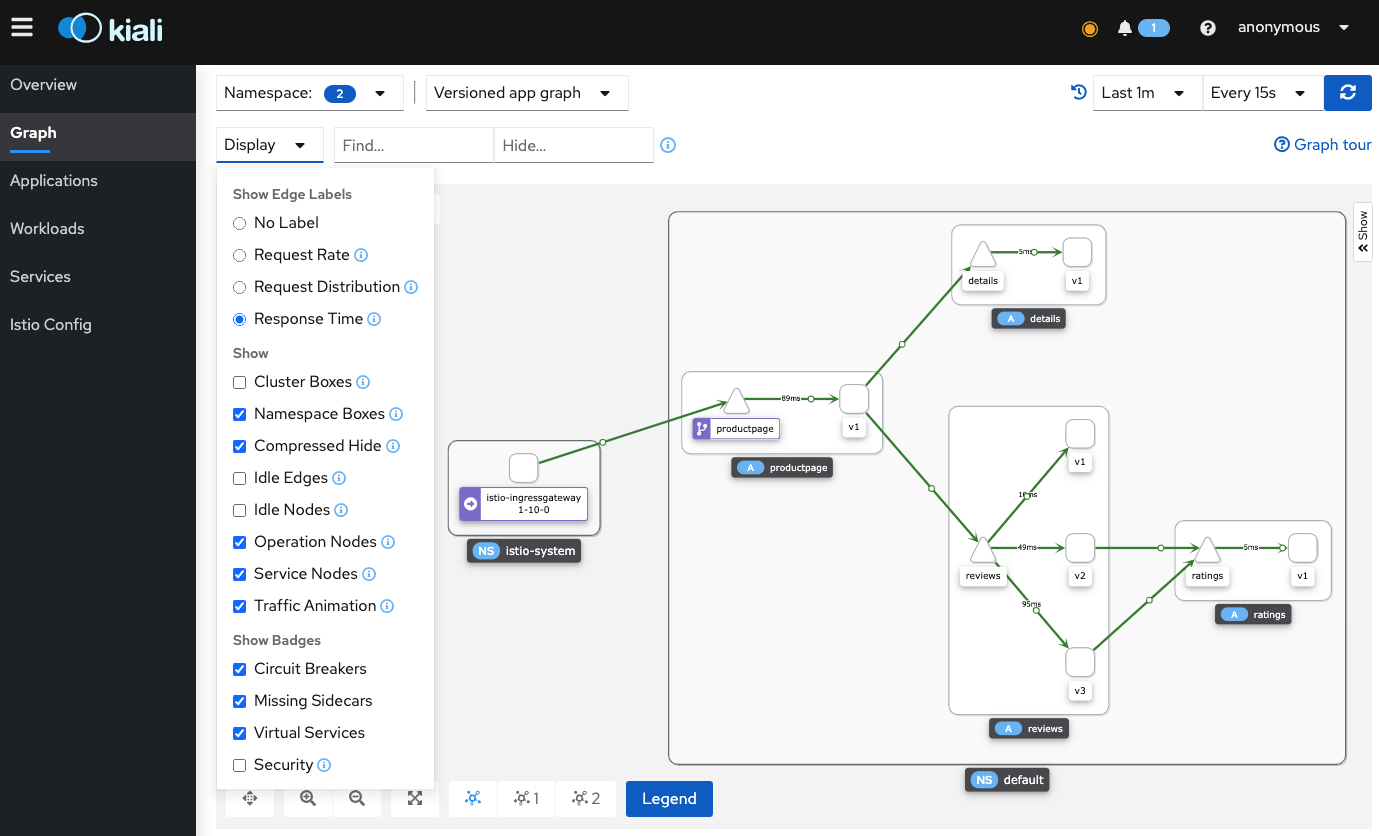
삭제
삭제전 터미널 창의 minikube tunnel, Kiali 대시보드를 정지한다.
- Bookinfo 삭제
$ samples/bookinfo/platform/kube/cleanup.sh
namespace ? [default]
using NAMESPACE=default
virtualservice.networking.istio.io "bookinfo" deleted
gateway.networking.istio.io "bookinfo-gateway" deleted
Application cleanup may take up to one minute
service "details" deleted
serviceaccount "bookinfo-details" deleted
deployment.apps "details-v1" deleted
service "ratings" deleted
serviceaccount "bookinfo-ratings" deleted
deployment.apps "ratings-v1" deleted
service "reviews" deleted
serviceaccount "bookinfo-reviews" deleted
deployment.apps "reviews-v1" deleted
deployment.apps "reviews-v2" deleted
deployment.apps "reviews-v3" deleted
service "productpage" deleted
serviceaccount "bookinfo-productpage" deleted
deployment.apps "productpage-v1" deleted
Application cleanup successful
2. Istio 삭제
# addon 삭제
$ kubectl delete -f samples/addons
# IstioOperator 삭제
$ kubectl delete istiooperators.install.istio.io -n istio-system istio-controlplane-1-10-0
istiooperator.install.istio.io "istio-controlplane-1-10-0" deleted
# 삭제 전 체크
$ istioctl x precheck
✔ No issues found when checking the cluster. Istio is safe to install or upgrade!
To get started, check out <https://istio.io/latest/docs/setup/getting-started/>
# Istio CR 삭제
$ istioctl x uninstall --revision 1-10-0
There are still 2 proxies pointing to the control plane revision 1-10-0
...
Proceed? (y/N) y
Removed HorizontalPodAutoscaler:istio-system:istio-egressgateway.
...
Removed MutatingWebhookConfiguration::istio-sidecar-injector-1-10-0.
✔ Uninstall complete
# 남아있는 Istio CRDs 삭제
$ istioctl manifest generate | kubectl delete -f -
customresourcedefinition.apiextensions.k8s.io "authorizationpolicies.security.istio.io" deleted
customresourcedefinition.apiextensions.k8s.io "destinationrules.networking.istio.io" deleted
...
# 사이드카 인젝션을 위한 레이블 삭제
$ kubectl label ns default istio.io/rev-
namespace/default labeled
참고